Guardium Vulnerability Assessment
Identify threats in minutes. Achieve greater efficiency and simply operations with built-in workflows.
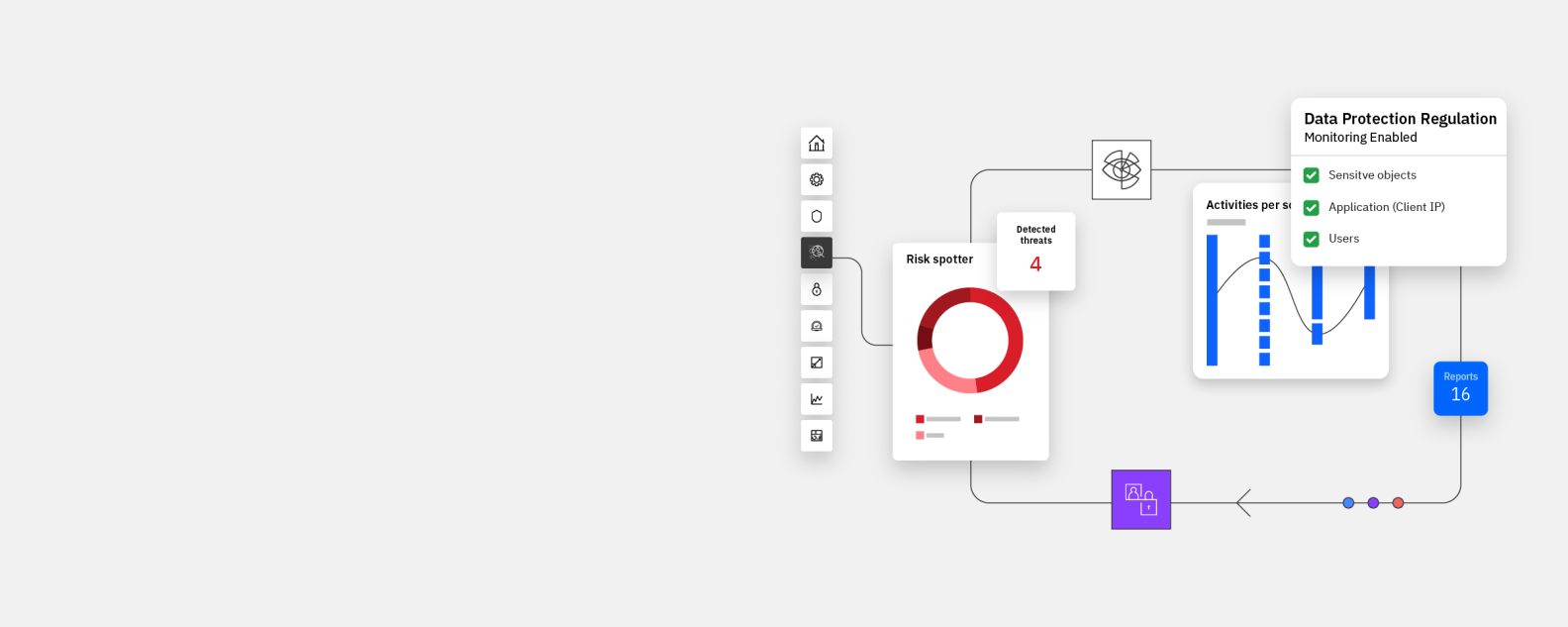
IBM Guardium Vulnerability Assessment software scans on-premises and cloud database infrastructure to detect vulnerabilities and orchestrate remedial actions. It is part of the IBM Guardium family of data security software.
Identify threats and security gaps in environments
Identifying vulnerabilities in your data environments is key to understanding and managing your data security posture. IBM® Guardium® Vulnerability Assessment scans data infrastructure such as databases, data warehouses, and big data environments — both on-premises and in the cloud — to detect vulnerabilities and suggest remedial actions based on benchmarks from STIG, CIS, CVE, and other configuration standards.
Guardium Vulnerability Assessment identifies security gaps in databases such as missing patches, weak passwords, unauthorized changes, misconfigured privileges, excessive administrative logins, unusual after-hours activity, and other behavioral vulnerabilities such as account sharing. It then provides full reports as well as actionable recommendations to address vulnerabilities to harden your database environments.
Guardium Vulnerability Assessment is delivered as a part of Guardium Data Protection, but can be implemented as a stand-alone offering that serves its own use case.
Why Guardium
Benefits

Achieve greater efficiency
Perform vulnerability assessments within minutes, with minimal read-only access privileges, with zero to minimal performance impact.

Simplify operations
Dynamic reports and precise recommendations for remediating data-centric threats and vulnerabilities.

Scalable platform
Scale from one data source to tens of thousands across multiple data centers or geographical locations. Support leading database platforms and all major operating systems, including big data environments.

Comprehensive enterprise support
Integrate or complement existing security solutions, IT systems, and applications such as ServiceNow. Whether its efficiently assigning tickets or enabling on-demand rescans users a streamlined and expedited vulnerability scanning and remediation workflow.”

Better understand and improve data security posture
Understand the latest vulnerabilities for supported platforms with automatic, real-time updates updates, summary results, and concrete recommendations.
Features
Best practice recommendations
Conduct in-depth tests based on criteria and benchmarks from STIG, CIS, plus other configuration standards, as well as support for SCAP. Harden your databases using hundreds of preconfigured tests according to best practices. Custom dashboard reports and drill-down capabilities are available for each major test. Database protection knowledge base subscription allows you to leverage automatic updates from the IBM Guardium Vulnerability Assessment development and research team about the latest vulnerabilities.

Data Security Posture Management
Scan data infrastructure for vulnerabilities to identify security risks, such as missing patches, weak passwords, incorrectly configured privileges and default vendor accounts. Evaluate and document your database security to help assess, escalate, and remediate risks. Plan scanning to understand zero-day threat exposures and remediate threats. ServiceNow integration allows for seamless orchestration and remediation.

Custom dashboard reports
Scan your entire database infrastructure for vulnerabilities to identify security risks and schedule platform-specific tests that detect insecure configurations for the specific database being assessed, along with drill-down capabilities. IBM Guardium Vulnerability Assessment is designed to provide detailed reports for more than 2,000 pre-defined and custom exposure tests. Monitor summary counts for each major test category: Center for Internet Security (CIS), Database Security Technical Implementation Guide (STIG) and Common Vulnerability Event (CVE).

Built-in compliance workflow
Provide a summary security evaluation, which includes weighted metrics and recommended remedial action plans to strengthen security. Automatically schedule assessments and manage report distribution, sign-offs, and escalations. Integrate the solution with other vulnerability management tools through APIs and/or a CSV upload for further correlations of vulnerabilities and risk. Use this to support regulations such as Sarbanes-Oxley, Payment Card Industry (PCI) and the Health Insurance Portability and Accountability Act (HIPAA).



Feel Interested? Contact Us For Details.
