Guardium DSPM (Data Security Posture Management)
Discover, classify, and protect your enterprise data across cloud and SaaS environments
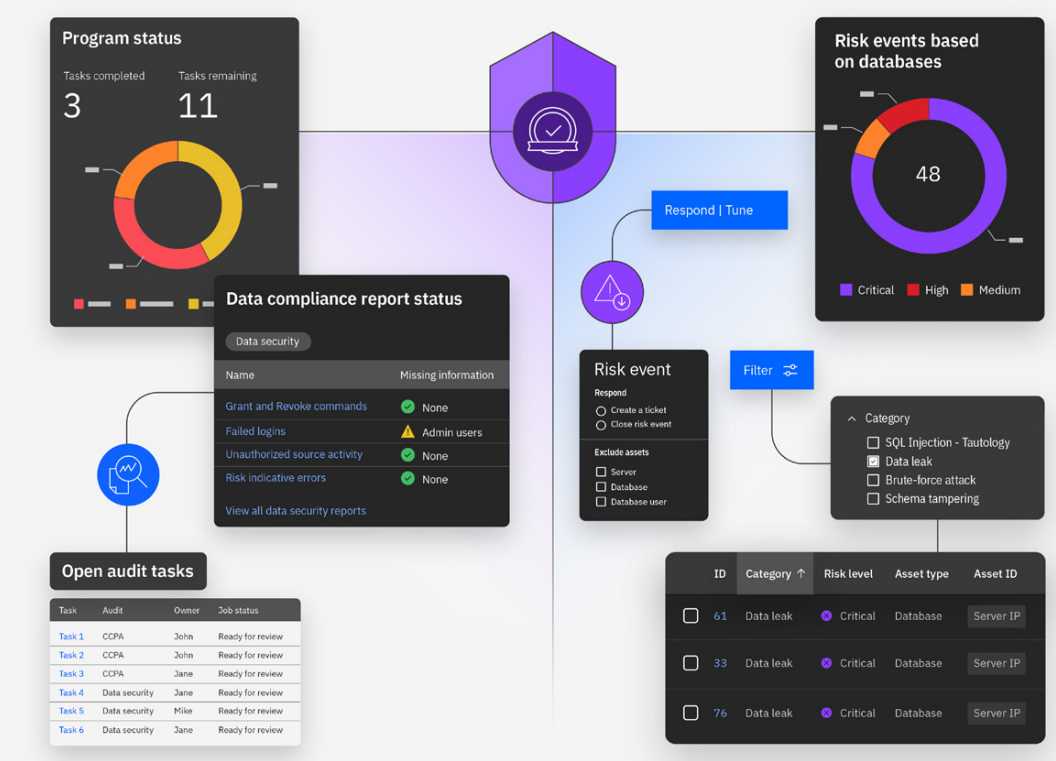
Take control of your data security in the cloud
As organizations adopt more sophisticated technology and development practices, increasing volumes and dispersion of data have made data security a challenge of extraordinary proportions.
Inadequate data security strategies significantly increase the risk of data leaks, breaches, unauthorized access to sensitive data, and substantial penalties for non-compliance with data privacy regulations. Available in IBM® Guardium® Data Security Center, IBM® Guardium ® DSPM discovers, classifies, and monitors sensitive data across cloud environments and SaaS applications, addressing several critical challenges:
Data sprawl – Discover and classify all cloud data, including “shadow data”, to pinpoint its precise location, track its movement, and manage access to it.
Shrinking attack surface – Remove publicly exposed sensitive data in hybrid cloud environments and SaaS apps.
Compliance & privacy – Ensure adherence to regulatory requirements concerning data privacy.
Resource optimization – Enhance efficiency and reduce cloud costs within cloud infrastructures.
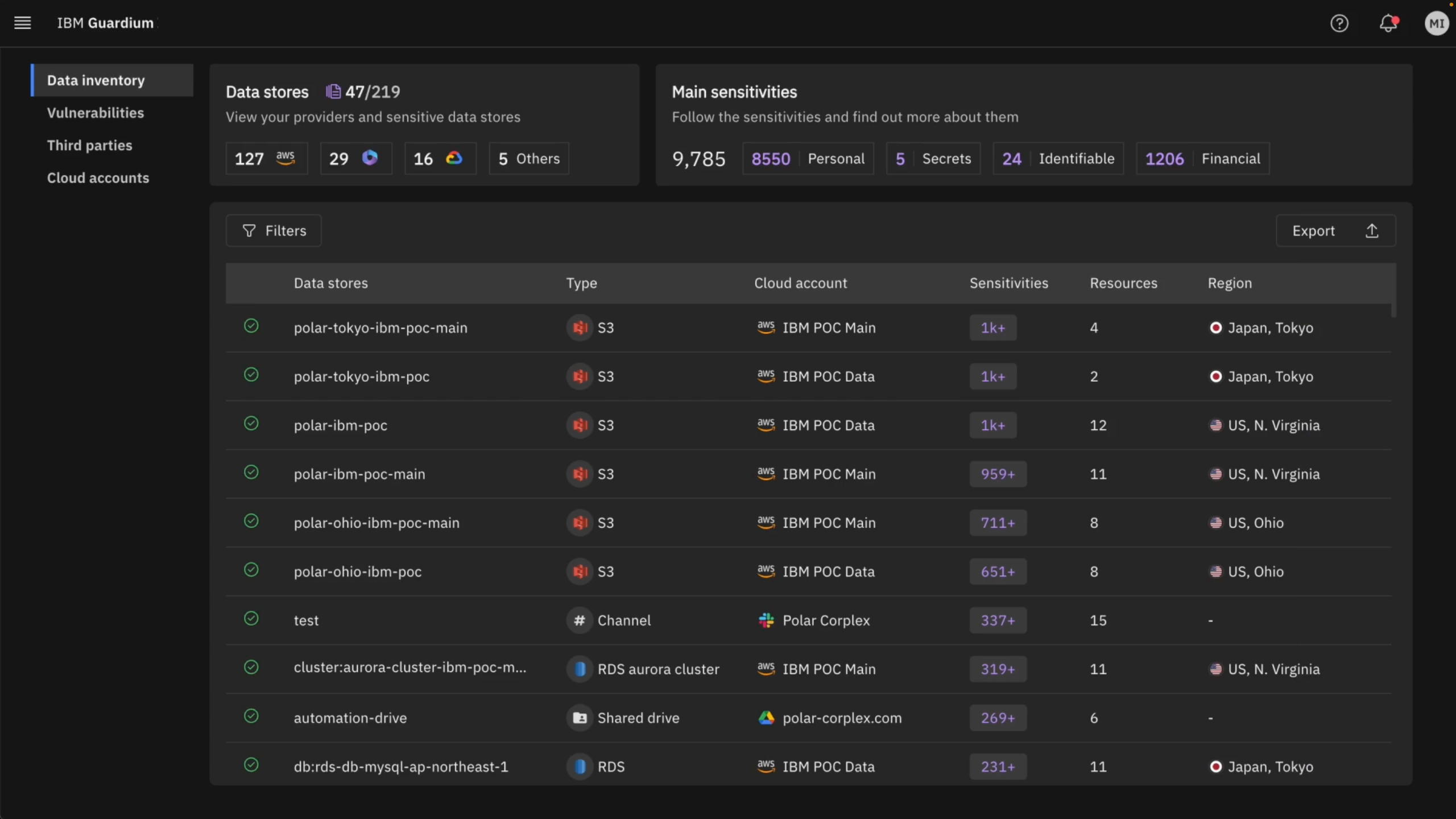
Bad data security posture is costly
Unintended gaps in data security can lead to costly financial consequences. The annual IBM Cost Of A Data Breach report provides recommendations on steps that can help prevent costly mistakes.
4.88
4.88 million is the average cost of a data breach in USD.
1 in 3
breaches involve shadow data.
40%
of data breaches involved data stored across multiple environments.
Benefits

Automated AI-powered data discovery and classification
Quickly, accurately, and continuously identify sensitive data across your cloud environment. Our solution leverages an advanced AI-powered engine to efficiently discover and classify sensitive data, saving you valuable time and resources. Thanks to its agentless deployment, DSPM begins discovery instantly—no prior knowledge of data locations or passwords is required.

Mitigating data risks and vulnerabilities
DSPM proactively detects and prevents data leakage between accounts and environments, while automatically identifying and remediating exposed secrets. Our innovative ransomware vulnerability detection engine, leveraging data flow analysis and access intelligence, provides unparalleled protection against potential threats and hazards.

Identify malicious data access
Gain comprehensive visibility into third-party data access to proactively identify and mitigate potential risks. Our AI-infused features streamline the process of vendor assessments, detect anomalies, and assess the potential impact of data breaches. This helps to ensure compliance with industry regulations and protect your organization from unauthorized access.
Use cases
3rd-party risk
Execute 3rd-party risk assessment of cloud data
Vendor assessment is a critical task for GRCs looking to govern their data and ensure it is secure and compliant, but tackling this process with manual operations can be extremely complex and time-consuming. DSPM provides its users with a clear view of all 3rd-party vendors with access to sensitive data and overly permissive roles across your cloud and SaaS environments. Empower both GRC and security teams with reports and actionable insights on vendor data access levels, ensuring compliance and safeguarding sensitive information.
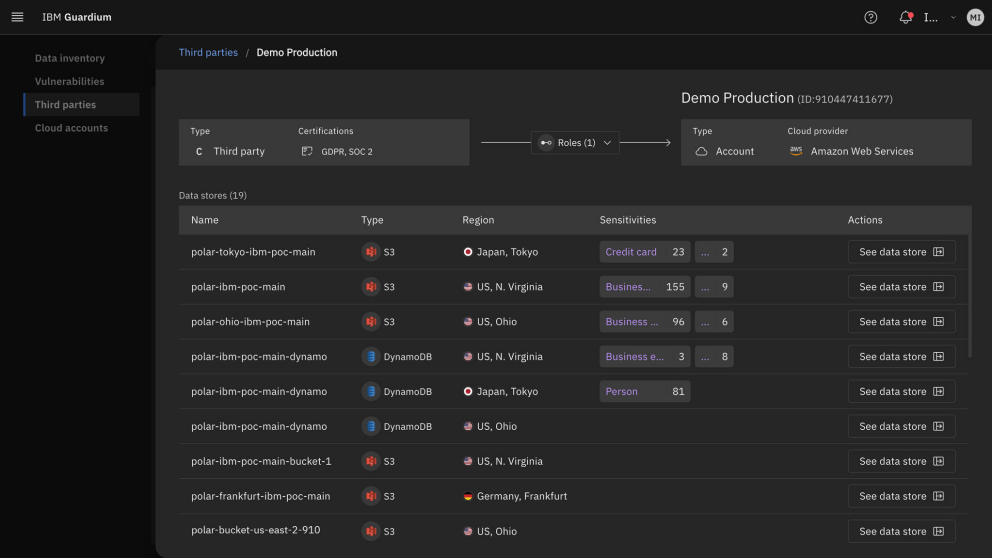
Sensitive Data
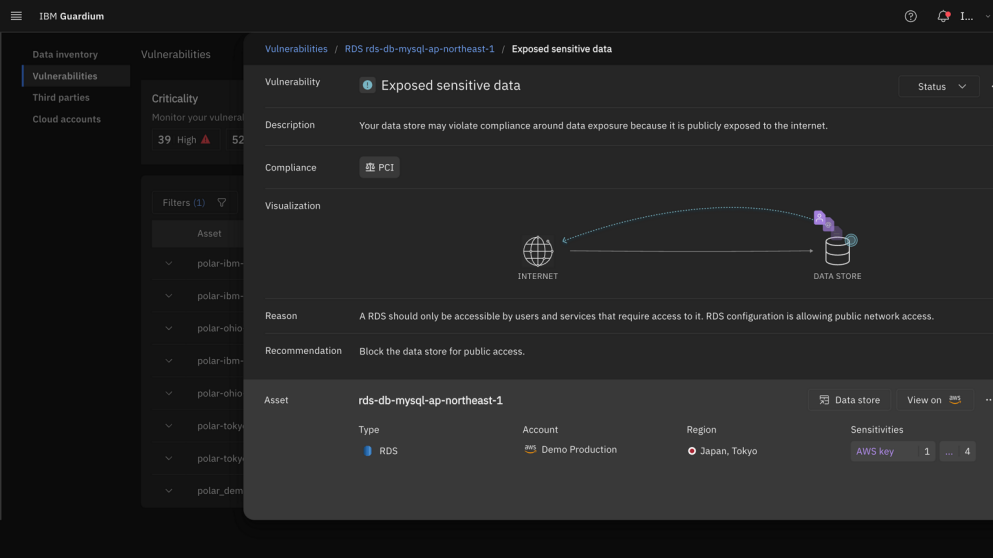
Remove publicly exposed sensitive data in the cloud
Secure your sensitive data from public exposure across sprawling cloud and SaaS environments. The discovery engine will not only detect known data stores but also surfaces hidden shadow data, including legacy and orphan repositories. By mapping potential attack paths to this sensitive information, you gain continuous visibility and the tools to comprehensively mitigate risk. Additionally, the platform ensures compliance with regulations like GDPR, HIPAA, CCPA, and more, by continuously monitoring data access and enforcing security policies, automatically generating audit reports, and alerting you about any potential compliance violations in real-time. This reduces the chance of costly data breaches and protects your brand reputation.
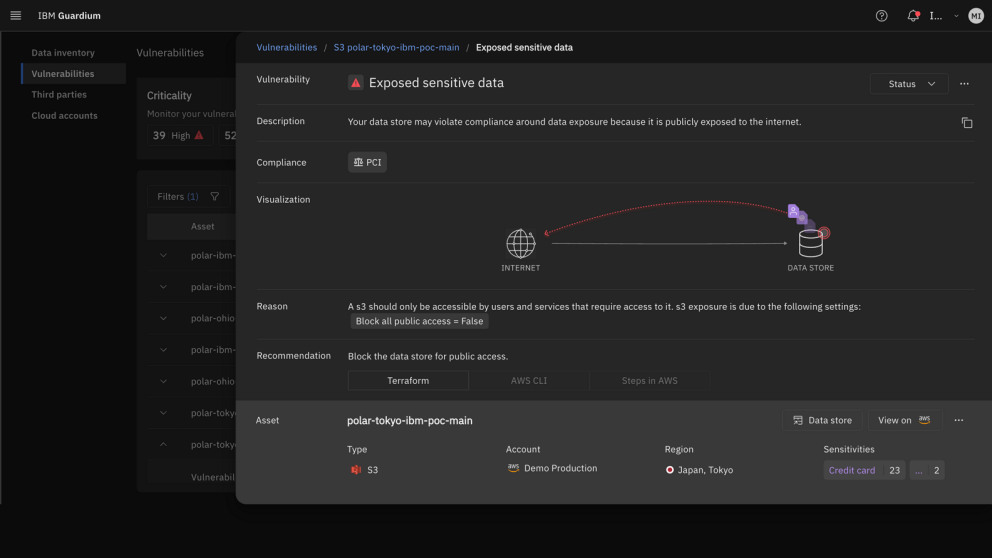
Ransomware
Protect production data against ransomware
Protect your production data from ransomware attacks across multicloud and SaaS environments. Continuously identify vulnerable data stores that lack encryption and robust backup processes. Our ransomware vulnerability detection engine, powered by advanced data flow graphs and access intelligence, prioritizes sensitive data based on context, ensuring data protection efforts are in focus.
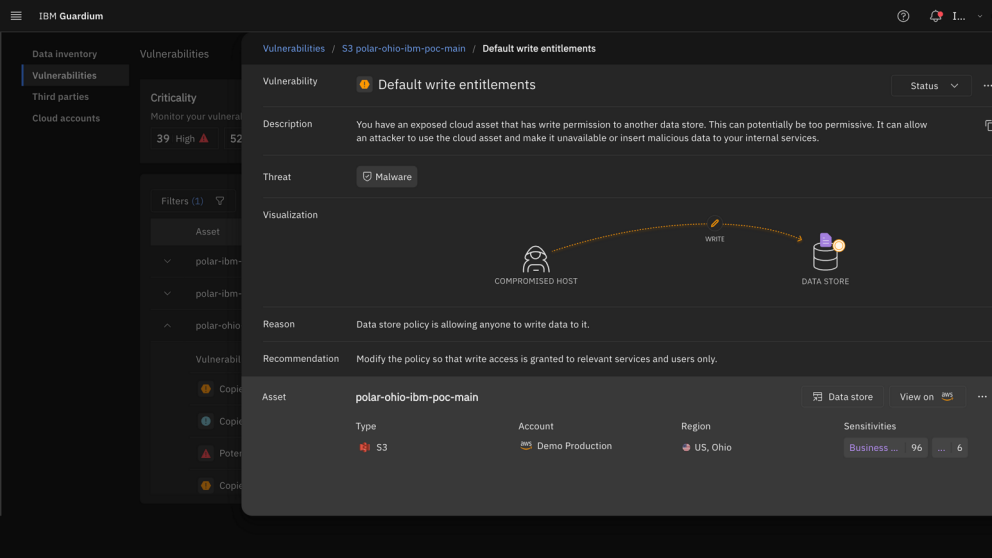
Data access control
Tighten data access control using by identity intelligence
Gaining visibility into the identities accessing sensitive data in multi-cloud and SaaS environments (such as employees or services) is a manual process that takes time and effort and is not scalable. Guardium DSPM accelerates and streamlines this process by automating data discovery and classification, mapping identities and their data flows, and providing continuous intelligence on identity-to-data access across your entire ecosystem. It also enables organizations to create and enforce data access policies that align with regulatory requirements, automatically detecting and remediating non-compliant anomalies to maintain a robust compliance posture.
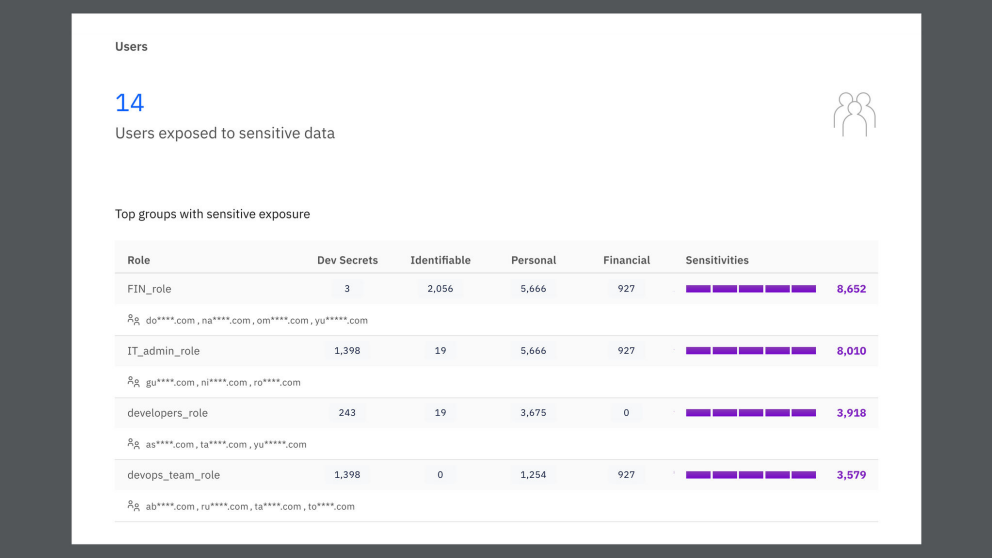
Exposed secrets
Detect and resolve exposed secrets across your cloud and SaaS
Organizations struggle to manually discover and remediate exposed secrets, risking data breaches and compliance violations. Guardium DSPM automatically and continuously scans cloud and SaaS environments to identify and classify secrets, enriching risk assessments by understanding the impact on sensitive data.
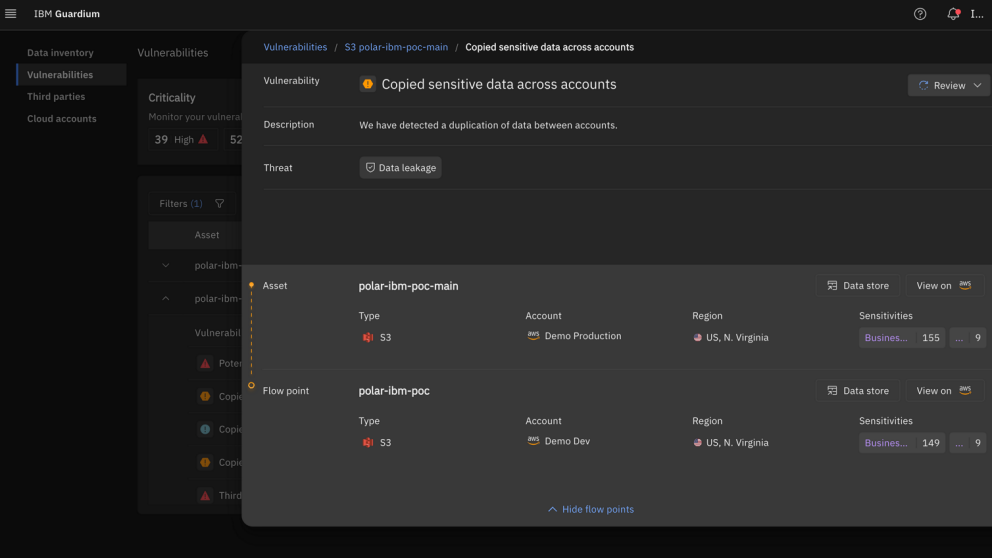
Data leakage
Detect and resolve data leakage from production to development environments
Our autonomous data lineage engine tracks and identifies unauthorized or anomalous movements that result in data leakage. It can detect data leaking between high to low environments, between cloud providers, cloud accounts and SaaS environments. This allows you to gain full visibility into your data landscape, detect potential leaks early and proactively secure sensitive information.
Take the next step
Get a 360-degree view of all your sensitive data in the cloud by discovering shadow data, analyzing the flow of data and uncovering posture vulnerabilities. Contact us for more details.
Explore Guardium


Feel Interested? Contact Us For Details.
