
Cloud Access Security Broker (CASB)
CASB provides IT managers with comprehensive insight into their organization’s cloud application usage, covering both sanctioned and unsanctioned (Shadow IT) applications. Cato’s CASB enables the assessment of each SaaS application to evaluate its potential risk, and the definition of highly granular and flexible access rules to ensure least-privilege and minimal risk exposure.
Eliminating Shadow IT
Full Cloud Application Visibility and Shadow IT Control
Admins responsible for controlling enterprise exposure to risks are often unable to manually validate each cloud application compliance. Using automated data collection and ML-based analysis, Cato CASB provides a calculated risk score for every cloud application. Presented in a Cloud App Catalog, each application profile is enriched with a description, compliance adherence, and security controls of the application. Admins can view all the information required to make informed decisions regarding application usage and define policies that limit risk and exposure. For example, preventing access to applications above a certain risk score, applications without MFA and SSO, apps that don’t comply with security standards, etc.
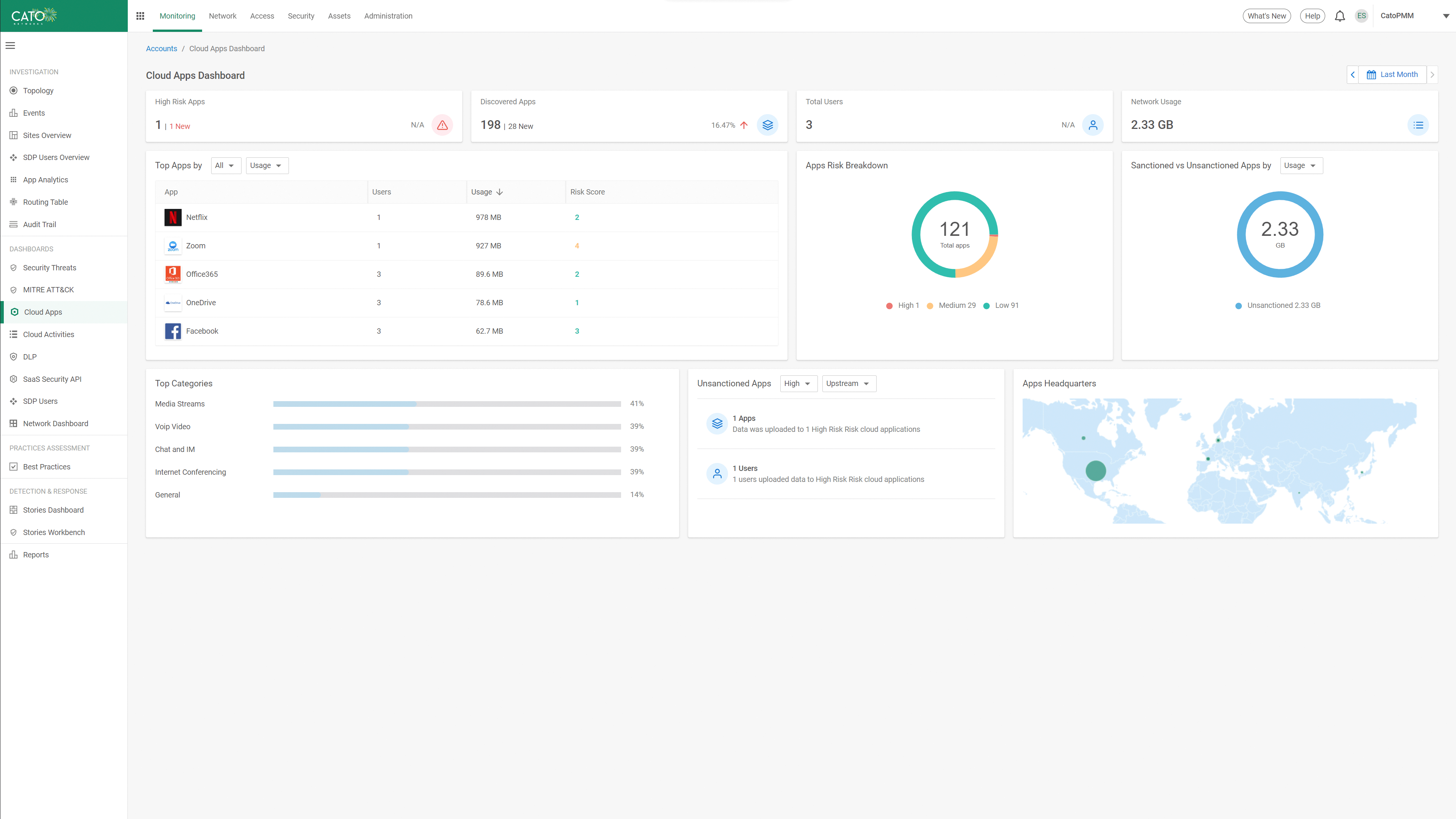
AI/ML-based Application Risk and Access Control
Admins responsible for controlling enterprise exposure to risks are often unable to manually validate each cloud application compliance. Using automated data collection and ML-based analysis, Cato CASB provides a calculated risk score for every cloud application. Presented in a Cloud App Catalog, each application profile is enriched with a description, compliance adherence, and security controls of the application. Admins can view all the information required to make informed decisions regarding application usage and define policies that limit risk and exposure. For example, preventing access to applications above a certain risk score, applications without MFA and SSO, apps that don’t comply with security standards, etc.
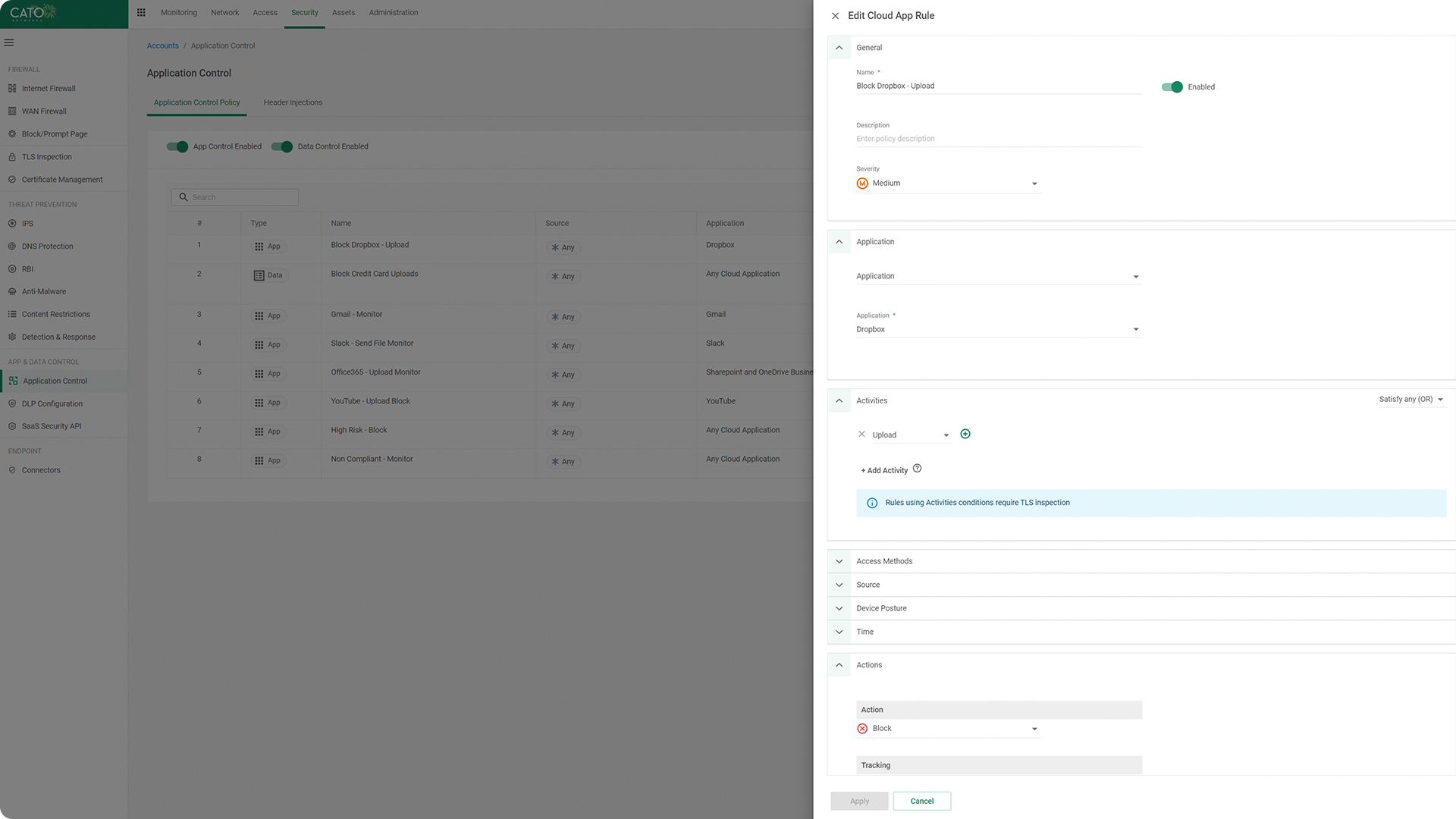
Controlling What Users Do Within Cloud Applications
Admins responsible for controlling enterprise exposure to risks are often unable to manually validate each cloud application compliance. Using automated data collection and ML-based analysis, Cato CASB provides a calculated risk score for every cloud application. Presented in a Cloud App Catalog, each application profile is enriched with a description, compliance adherence, and security controls of the application. Admins can view all the information required to make informed decisions regarding application usage and define policies that limit risk and exposure. For example, preventing access to applications above a certain risk score, applications without MFA and SSO, apps that don’t comply with security standards, etc.

Inline and Out-of-Band Application Access Controls
Users access cloud applications both in the office and remotely, and from corporate devices and BYOD, requiring out-of-band control inline controls. In addition to its inherent visibility and control of inline traffic, Cato CASB provides API connectors for common enterprise cloud applications. The API connectors allow near real-time monitoring of application access to protect from data leakage, data sharing misconfiguration, and malware propagation. With Cato CASB operating both inline and out-of-band, the admin’s visibility, and control of cloud app usage is comprehensive and complete, enabling consistent control in all application access scenarios.
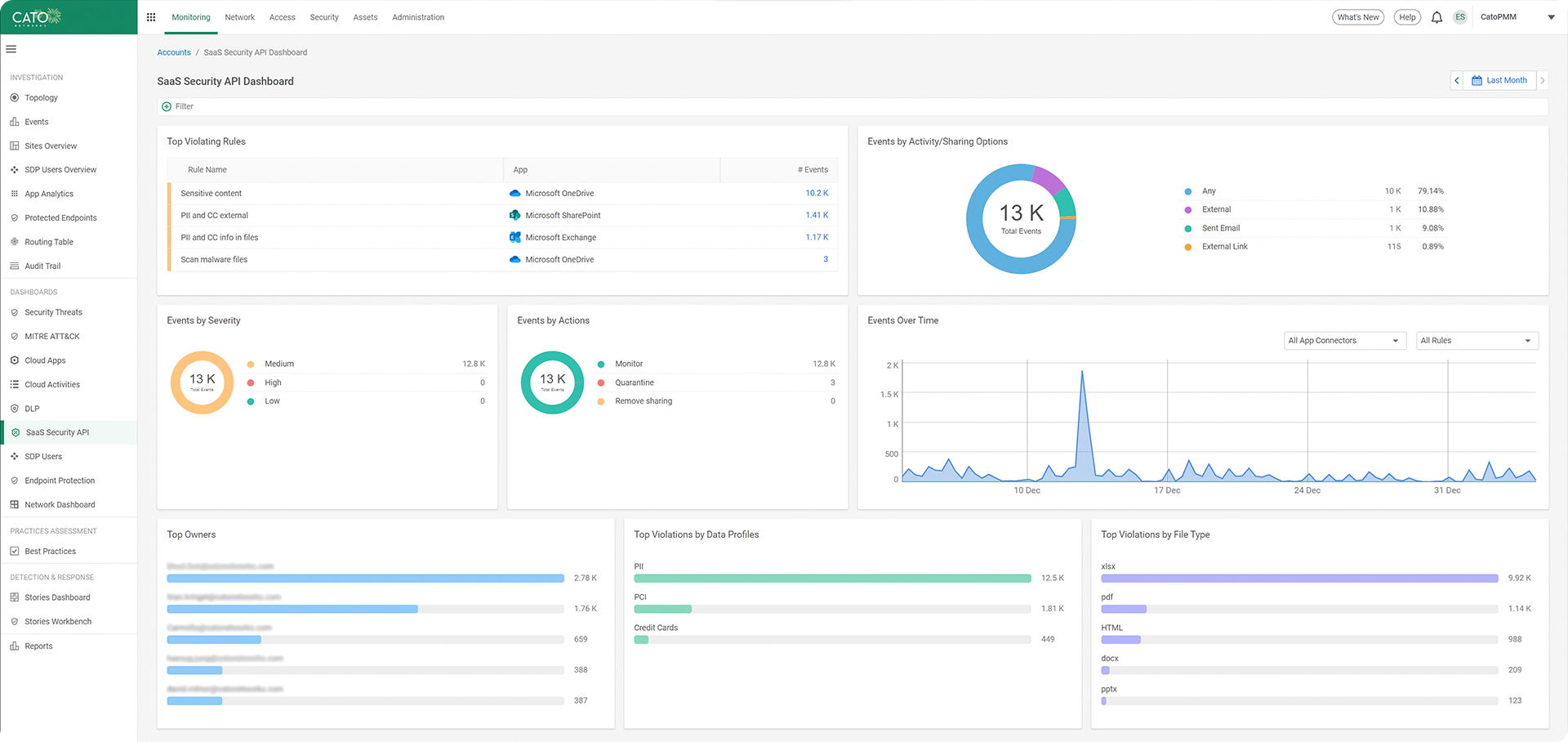
Stop Data Leaks with Enterprise SaaS Tenant Restriction
The same SaaS applications that are sanctioned and permitted by the enterprise may also be in private use by employees, posing a risk of sensitive data leakage. Following industry best practices, Cato CASB can limit access down to sanctioned tenants within sanctioned applications to ensure enterprise intellectual property doesn’t leak outside the enterprise without explicit permission.

The Strategic Benefits of a True SASE Platform
Architected from the ground up as a true cloud-native SASE platform, all Cato’s security capabilities, today and in the future, leverage the global distribution, massive scalability, advanced resiliency, autonomous life cycle management, and consistent management model of the Cato platform.

Consistent Policy Enforcement
Cato extends all security capabilities globally to deliver consistent policy enforcement everywhere and to everyone, from the largest datacenters down to a single user device.
Scalable and Resilient Protection
Cato scales to inspect multi-gig traffic streams with full TLS decryption and across all security capabilities, and can automatically recover from service component failures to ensure continuous security protection.
Autonomous Life Cycle Management
Cato ensures the SASE cloud platform maintains optimal security posture, 99.999% service availability, and low-latency security processing for all users and locations, without any customer involvement.
Single Pane of Glass
Cato provides a single pane of glass to consistently manage all security and networking capabilities including configuration, analytics, troubleshooting, and incident detection and response. Unified management model eases new capabilities adoption by IT and the business.

Feel Interested? Contact Us For Details.
