
Third-party Risk Management
Manage third-party risk across your digital supply chain
THIRD-PARTY RISK MANAGEMENT
Working with vendors can be your win.
Vendors and third-party partners help your business grow and stay competitive, but they also expose you to cyber risk. That’s because malicious attackers look for the weakest links in an organization’s security posture. Often, this resides in your company’s interconnected supply chain.
But by knowing these concerns, that means you can get ahead of them. Our solutions help you maintain control over your vendors, your vendors’ vendors, and so on, from onboarding and assessments, to threat monitoring and response, to offboarding. Stay ahead of threats by focusing your priorities, trusting our externally validated data and insights, and managing workflows from end to end. Showcase how your team keep third-party risks at bay.

End-to-end business outcomes.
70%
Reduction in vendor on-boarding time
1000+
75%
Reduction in probability of breach via third party
65K
Vendors in our network, growing at over 40% YoY
Featured third-party risk management solutions.
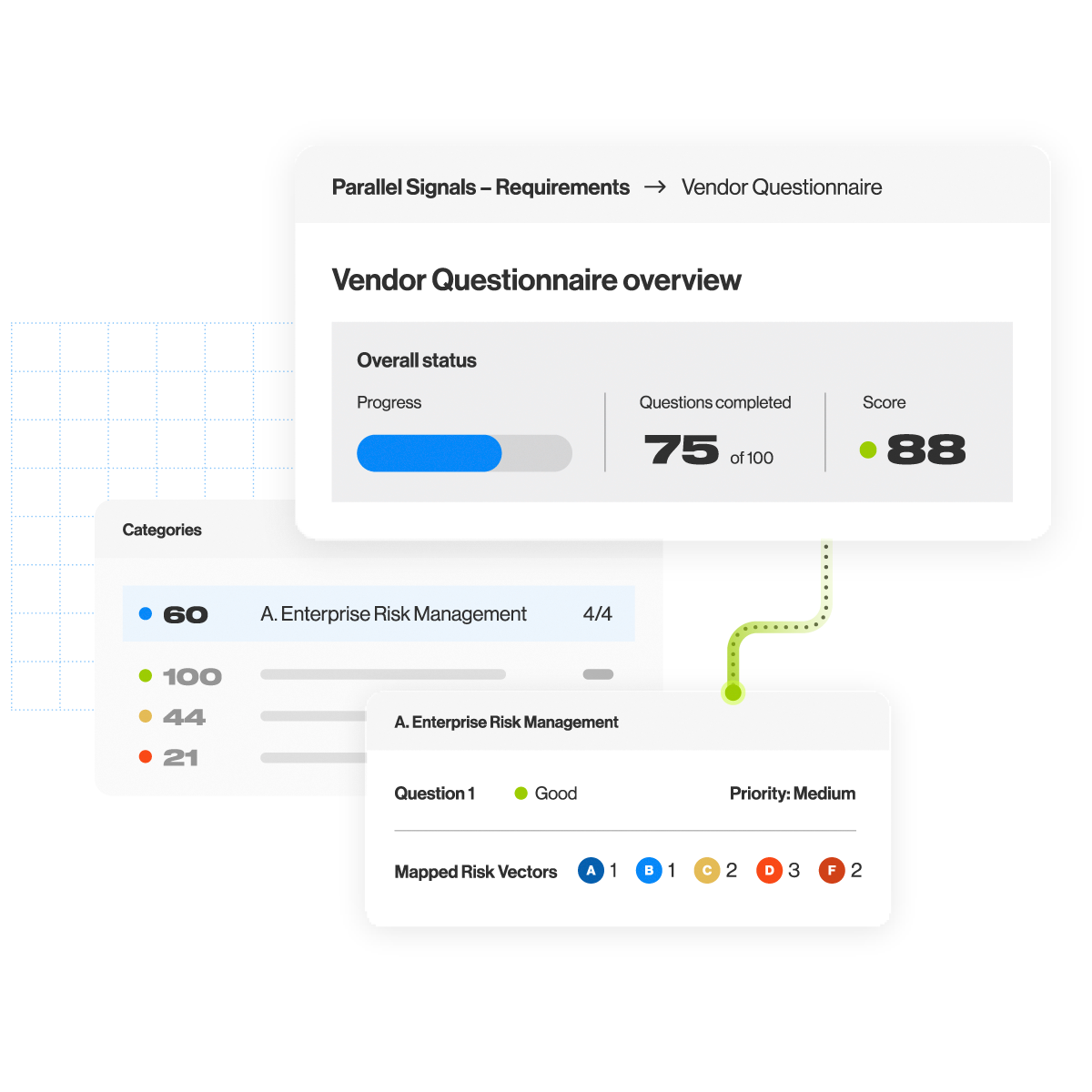
Vendor Risk Management
Assess more vendors, faster
Don’t let risk assessments be a bottleneck. With Vendor Risk Management, you can ensure that third-parties are within your organization’s risk tolerance and manage hundreds of vendors as effectively as you manage ten.
- Increase efficiency with a network of over 65,000 vendor profiles (and growing)
- Accelerate onboarding with automated assessments
- Validate vendor responses with objective data and evidence
Continuous Monitoring
Stay up to date with your vendor network
Strike a balance between visibility and prioritization. Get a full view of your third and fourth parties without missing a step with Continuous Monitoring, while also improving the security posture of your vendor portfolio to instill trust.
- Detect and address ongoing third-party risk
- Remediate easily with supporting data and evidence
- Discover fourth-party product usage automatically
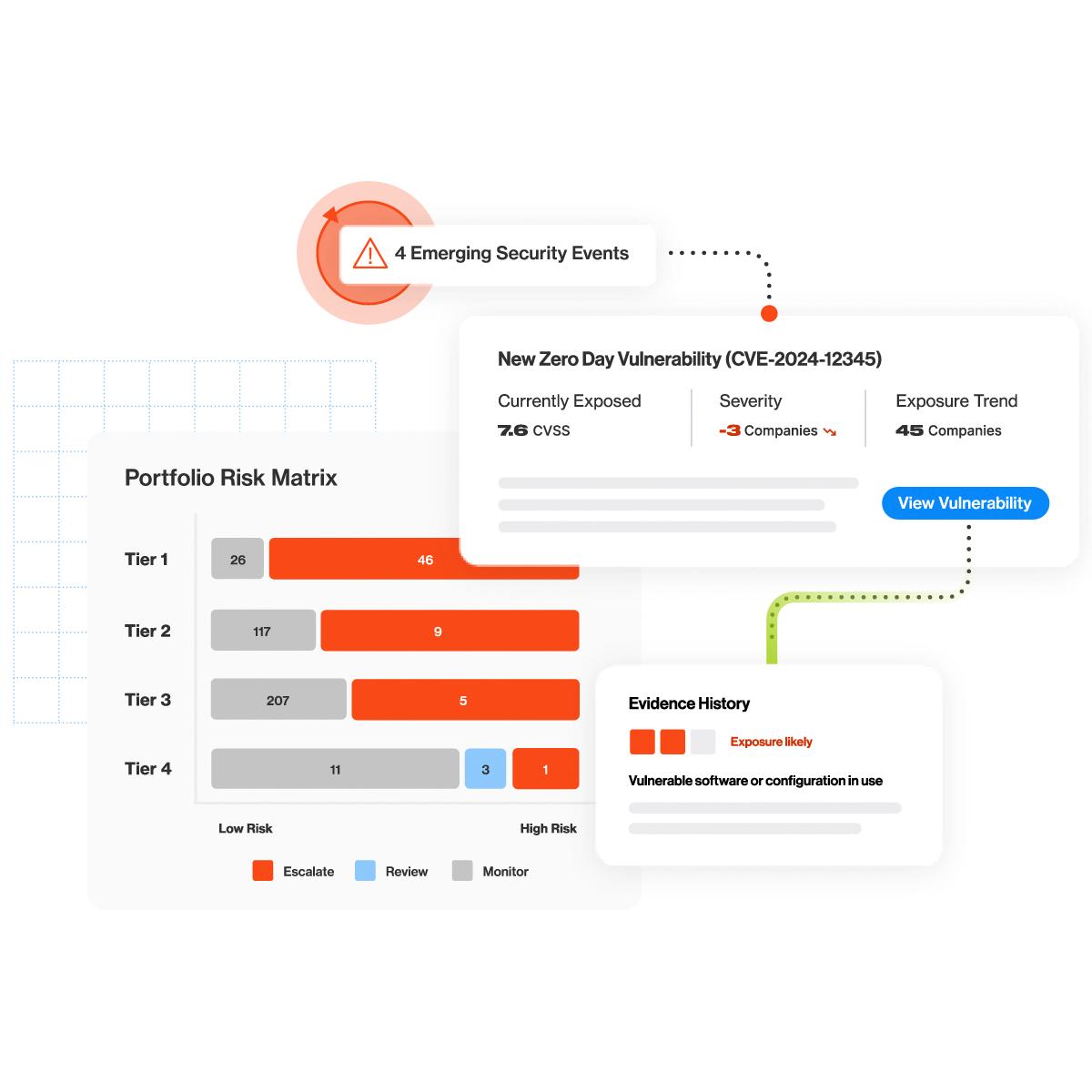
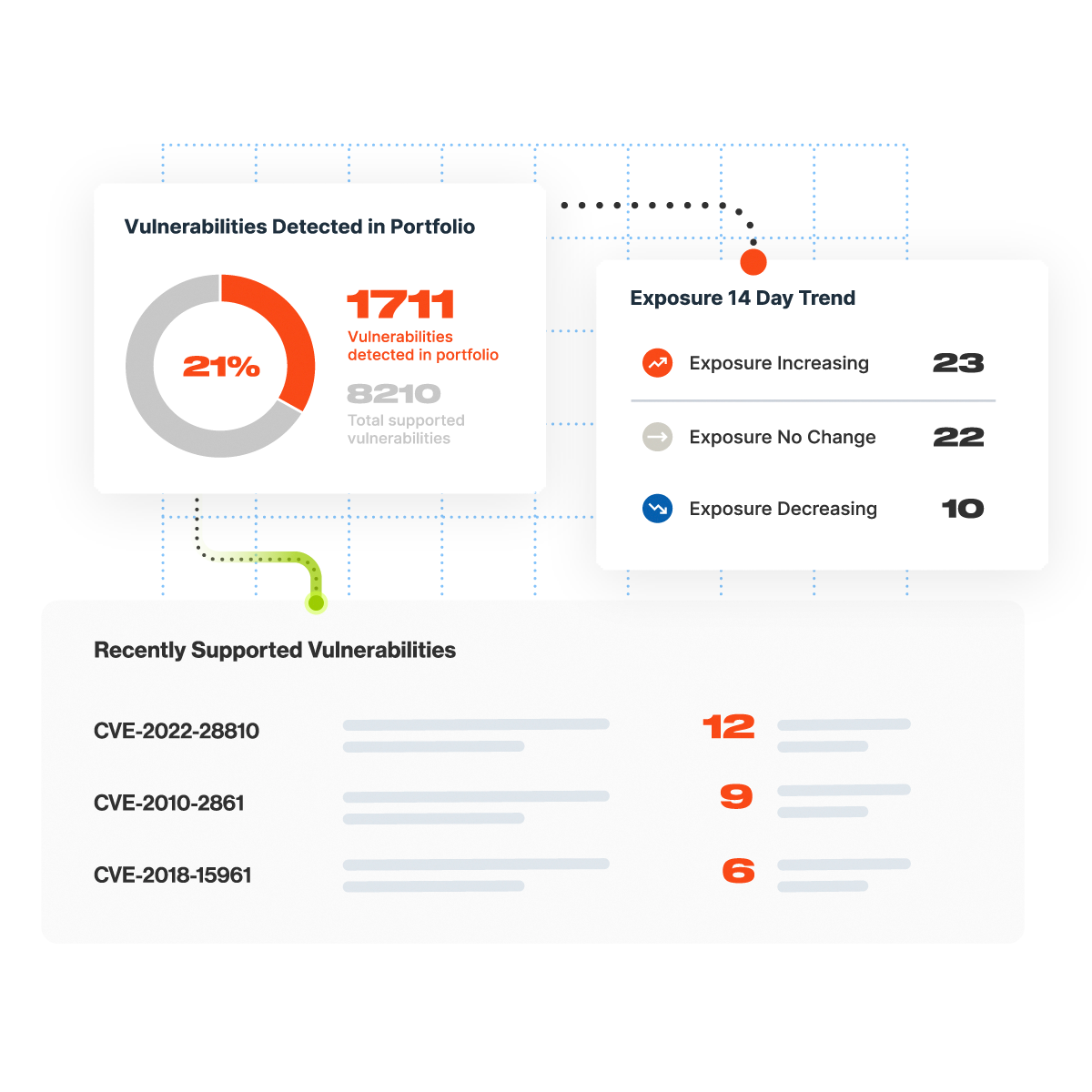
Vulnerability Detection
Detect and respond to zero-day vulnerabilities
As threats evolve, all eyes are on your digital ecosystem. Bitsight Vulnerability Detection & Response gives you the confidence to handle unforeseen major security events across third parties.
- Mitigate emerging zero day vulnerabilities at scale
- Improve efficiency and scalability of vendor outreach
- Focus on what matters most with real-time reporting
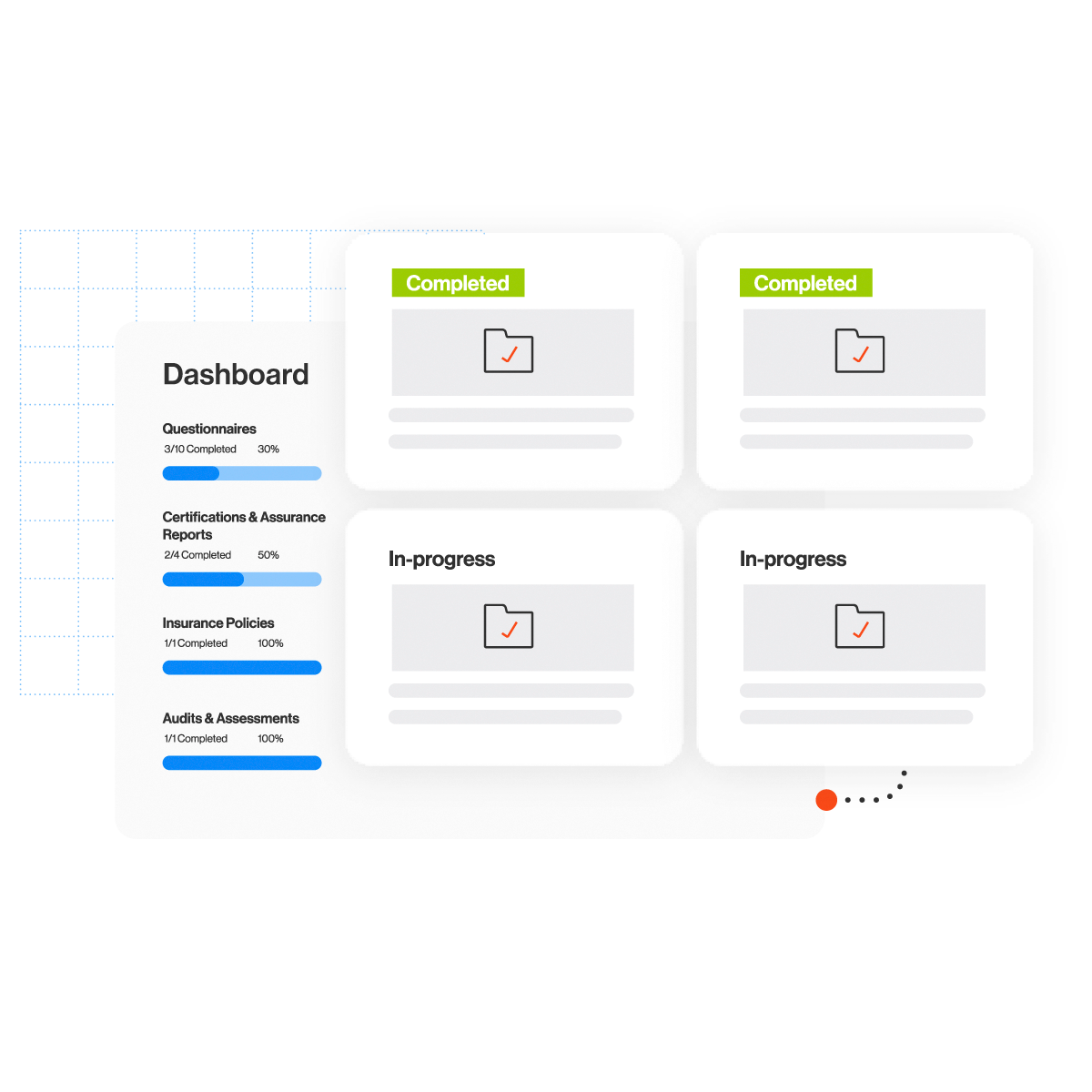
Trust Management Hub
Scale your customer security reviews
Security reviews and assessments are an unavoidable part of doing business, and for good reason. With Trust Management Hub, you can manage security review requests and share your information with just a few clicks, all through one intuitive portal.
- Let sales initiate sharing while you maintain full control of every document
- Prevent non-security staff from saving outdated documents
- Include questionnaires such as SIG Core and Lite, certifications like SOC and ISO, and attestations
Reveal, remediate, and monitor supply chain risk.

Market-leading
cyber risk data
Prioritize, mitigate, and report on risk across your portfolio.
Objective
universal standard
Leverage the only metrics verified to correlate to breaches.

Actionable
risk insights
Make risk-based decisions to improve efficiency and effectiveness.

Feel Interested? Contact Us For Details.
