
Cyber Threat Intelligence
Real-Time Cyber Threat Intelligence From The Clear, Deep & Dark Web
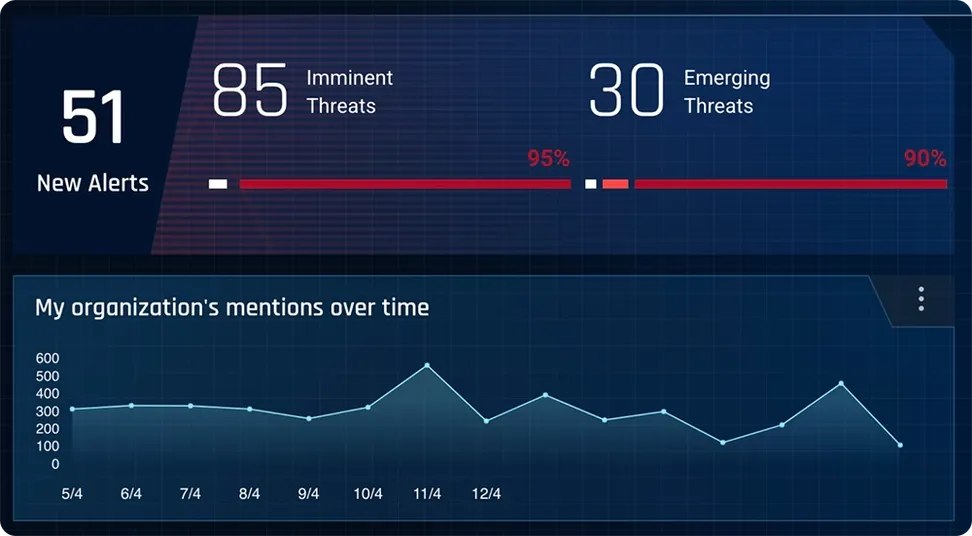
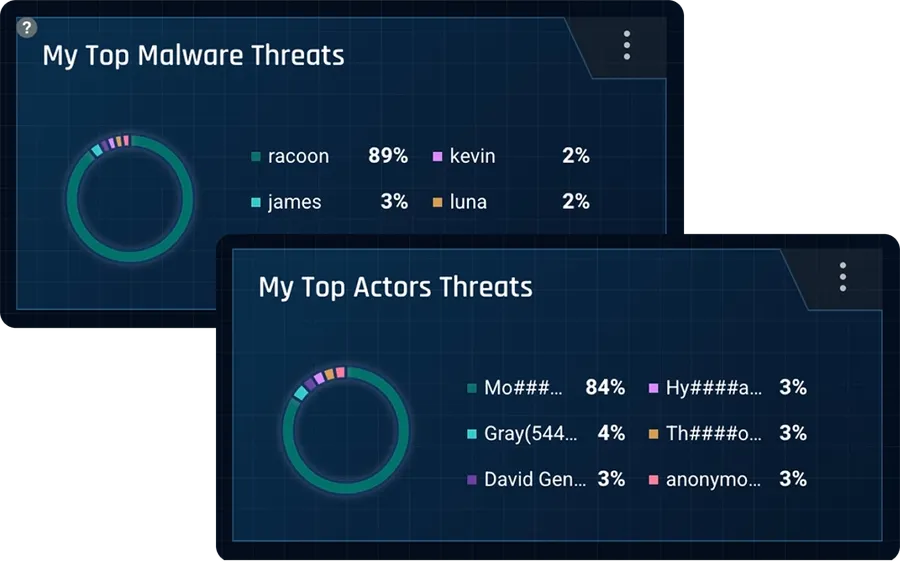
Cybersixgill collects 7 million intelligence items from over 1,000 underground forums and marketplaces daily. We track over 700 APT groups, 4,000 types of malware, 95 million threat actors and 6 million unique IOCs. We enrich this data with context to provide security teams with comprehensive insight into the nature and source of each threat in less than a minute following collection so they can detect and prevent cyber attacks before they happen.
Threat Intelligence
Capturing Potential Threats, IOCs, Tactics, Techniques and Procedures as They Surface
Access our collection of contextual threat intelligence from the deep, dark, and clear web as well as open source intel, to proactively block threats before they are weaponized in a cyber attack.
Extensive data collection
We uncover threat activities in any language, in any format and on any platform. Our data collection includes sources that are inaccessible to other threat intelligence vendors, such as complex CAPCHA, posts that have been deleted, invite-only instant messaging groups and dark web forums.
Delivering intel as it emerges
Automated crawlers infiltrate all clear, deep and dark web sources, extracting and enriching data across the threat landscape as it is posted. In less than 60 seconds following collection, intelligence items are displayed and available to security teams. It takes less than 1 hour from full activation to receive the first incoming alerts.
Threat intelligence that works for you
We make it easy to detect and understand threats by providing flexible delivery options for all use cases, personas and security maturity levels. We process an average of 5 million API queries per week and our Portal users are serving their teams with instant threat intel reports on any CTI topic in under 60 seconds.
Covert, safe access to the deep and dark web
Uncover threat actor activity in any language, format and platform with real-time access to the largest database of deep, dark and clear web activity on the market.

Key product features
The most extensive base of sources
Our data sources include limited-access forums, illicit underground markets, code repositories, paste sites, clear web sources, social media platforms and historical data extending to the 1990s.
Comprehensive threat actor profiles
We collect and monitor over 95 million threat actor profiles, detailing their languages, history, arenas of activity, TTPs, interests, peer networks and interactions.
Supports any language or data format
Our unique NLP & OCR algorithms process data in all languages and formats, with autonomous translation and image-to-text content extraction.
OSINT data
Access a broad range of reports, research and news from clear-web sources including cyber new sites and blogs, global news sites, national CERTS, ISACs and more.
Cybersixgill IQ
Use our powerful generative AI capability to simplify complex threat data, instantly generate finished reports and comparison tables or provide 24/7 assistance to make threat data easier to understand for every level of experience.
Streamline the investigation of multiple entities
Efficiently analyze, investigate and correlate diverse threat intelligence entities. Consolidate information about APTs, IoCs, malware and more in one place to eliminate the need for manual cross-referencing.

Turning Data Into Strategic Threat Intelligence With AI
Cybersixgill IQ, our powerful generative AI capability turns raw threat intelligence into human-readable, contextual summaries and finished reporting. Our threat intelligence platform also features an always-available AI assistant, instantly answering specific queries you may have to make threat intelligence more accessible to everyone at every level of experience.
Use Cases For Cyber Threat Intelligence
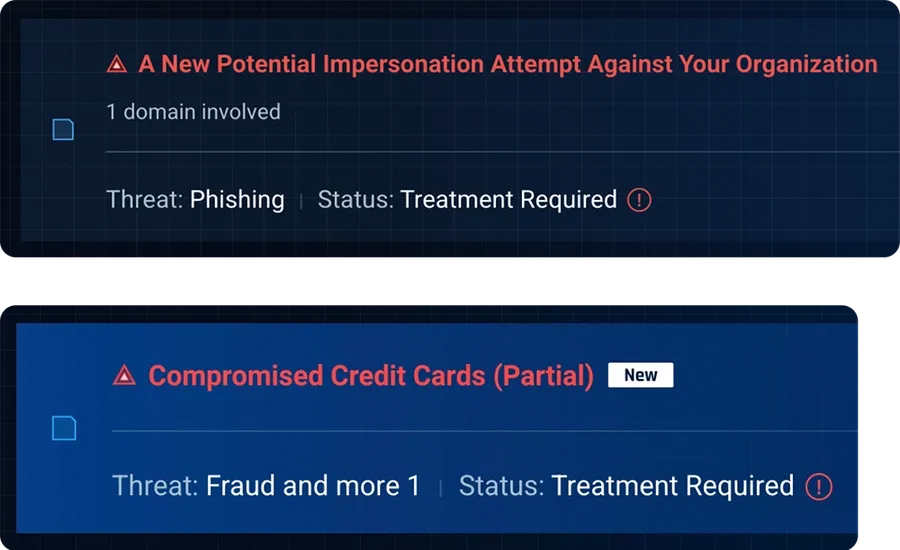
Compromised credentials, credit card & data leaks on the dark web
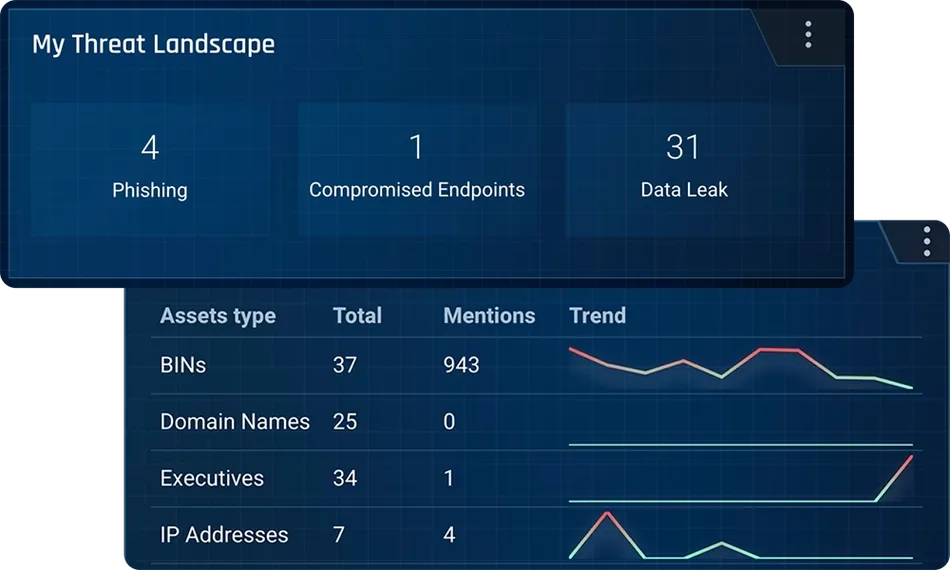
Set up customizable alerts to notify you of compromised employee credentials or customer data leaked on the deep and dark web. Search our data collection across multiple sources including instant messaging apps, IRC chats and limited-access dark web forums and marketplaces. Receive a breakdown of leaked credit cards by BINs, geography or issuer.
Ransomware & malware protection
Continuously monitor ransomware forums, markets and dedicated leaks sites (DLS) to provide critical insight regarding ransomware and malware operators. Monitor their capabilities, specialties and limitations in ransomware markets and get alerts as ransomware as a service (RaaS) operators extend their reach to promote their malware on the underground.
Threat monitoring & threat hunting
Use the secure dark web search engine capability within our threat intelligence platform to hunt for threats targeting your organization and learn more about their tactics techniques and procedures. Understand potential attack paths and threat actor motives to proactively prevent emerging cyber attacks before they are weaponized.
Brand protection
Detect real-time mentions of your brand across the cybercriminal underground and identify typosquatting activity which could affect your web domains. Receive early alerts regarding threat actor activity and discussions related to your company assets, products, management and credentials, whether in text or from images, as well as suspicious domains and brand abuse on rogue applications or app stores.
How our threat intelligence compares
| Cybersixgill | Other vendors | |
| Fully automated threat intelligence collection, extraction and indexing, minutes after it has surfaced | ✅ | Limited |
| Gains and maintains access to invite-only forums, messaging groups and closed marketplaces | ✅ | Limited |
| Ability to scrape data sources with complex CAPCHA and posts that have been deleted | ✅ | ✖ |
| Image/OCR extraction | ✅ | ✖ |
| Translates any language | ✅ | Limited |
| Generates detailed profiles on threat actors & groups, including aliases, hours of activity, peer networks, posts and areas of interest | ✅ | Limited |
| Provides unrestricted access to our complete body of threat intelligence | ✅ | Limited |
| Generative AI capability embedded throughout all solutions, sourcing intel in real-time from the deep and dark web, providing human-readable, contextual summaries, finished reporting and a personalized AI assistant. | ✅ | Limited |
Our CTI is available via a single or multi-tenancy SaaS Portal, API or integration
Investigative Portal
Safely and covertly access the deep and dark web via our threat intelligence platform for single or multi-tenancy users. Widely referred to as a dark web search engine, users can quickly uncover emerging risks, vulnerabilities or leaked data in real-time. The Investigative Portal is embedded with our generative AI assistant, helping users to build reports, answer queries and add context to your findings.
API & Feeds
Seamlessly integrate our cyber threat intelligence into existing workflows, systems or third-party solutions. Enhance remediation playbooks and workflows by enriching your existing security event logs with our data collection and enable comprehensive threat landscape analysis. Streamline repetitive tasks involved in SOC and threat hunting operations to facilitate proactive responses to emerging threats.
Integrations
Connect our CTI into your technology and enhance the performance of your security solutions. We partner with over 30 global organizations including Palo Alto, Snowflake, Anomali, Microsoft and Splunk, integrating our threat intelligence to support their cybersecurity solutions. We tailor each integration to meet specific use cases, improving operational efficiencies and delivering cost savings.
Our Data, Your Way
Cyber Threat Intelligence is available within our SaaS Portal that supports both single or multi-tenancy users, via API or integration into your existing technology.

Feel Interested? Contact Us For Details.
