
Exposure Management
Manage exposure across your entire attack surface
EXPOSURE MANAGEMENT
From your firewalls to the deepest corners of the dark web.
The more your attack surface expands, the harder it is to connect the dots on what’s putting your organization at risk. Which assets are most vulnerable? Which vendors are high risk? What threat activities are most relevant?
Bitsight gives you visibility into threats and exposures across parties and through the cybercriminal underground, so you can see and protect your entire digital infrastructure—on-prem, in the cloud, and across the supply chain.

Redefining how organizations see risk.
External Attack Surface Management
Visualize your attack surface
Discover unknown assets, identify and prioritize vulnerabilities, and see your digital infrastructure like your adversaries do with External Attack Surface Management.
- Automatically map your digital footprint from day one, including shadow IT and third-party vendor risks
- Prioritize remediation efforts based on real-world impact
- Use trusted metrics to generate executive-level reports that link cyber exposure to business outcomes

Continuous Monitoring
Map threats across your digital supply chain
Supply chain attacks, zero days, and other cyber threats don’t wait for annual questionnaires or reassessments. To stay ahead, use Continuous Monitoring to keep a pulse on your vendor ecosystem and proactively mitigate risk.
- Gain broad visibility into your extended attack surface, including fourth party vendors
- Use tangible, objective evidence to partner with your third parties for quicker remediation
- Communicate critical third-party risk insights across the company and to the board
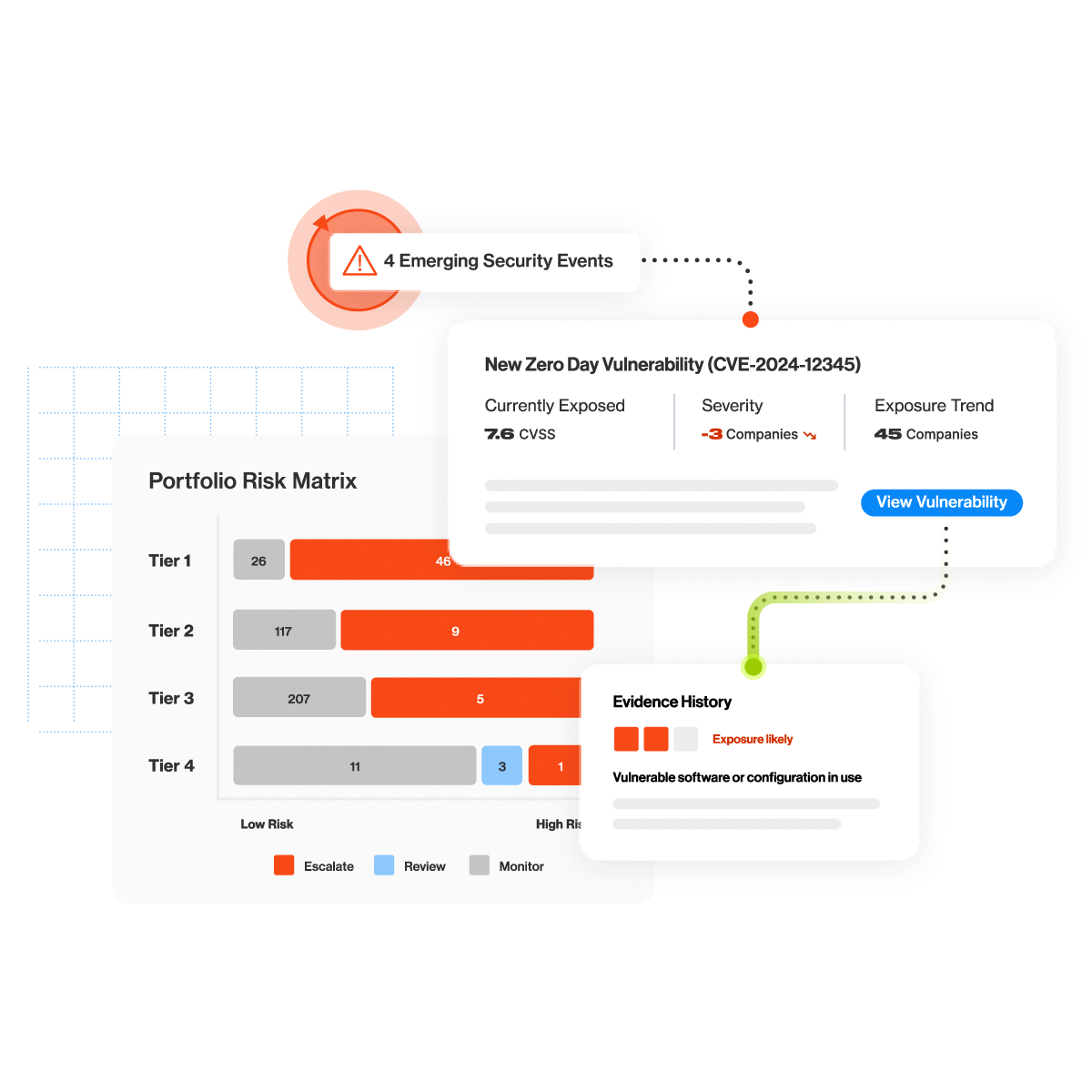
Cyber Threat Intelligence
Stay ahead with real-time intelligence
Take control of your organization’s risk with Cyber Threat Intelligence, which captures, processes, and alerts teams to emerging threats, TTPs, IOCs, and their risk exposure as it surfaces. We collect 7 million intelligence items daily from over 1,000 underground forums and marketplaces.
- Use AI-driven enriched insights provide security teams with information about the source of threats in less than a minute
- See real-time findings from some of the most common risk areas—including compromised credentials, vulnerabilities, ransomware, adversaries
- Leverage customizable alerts for your highest risk areas

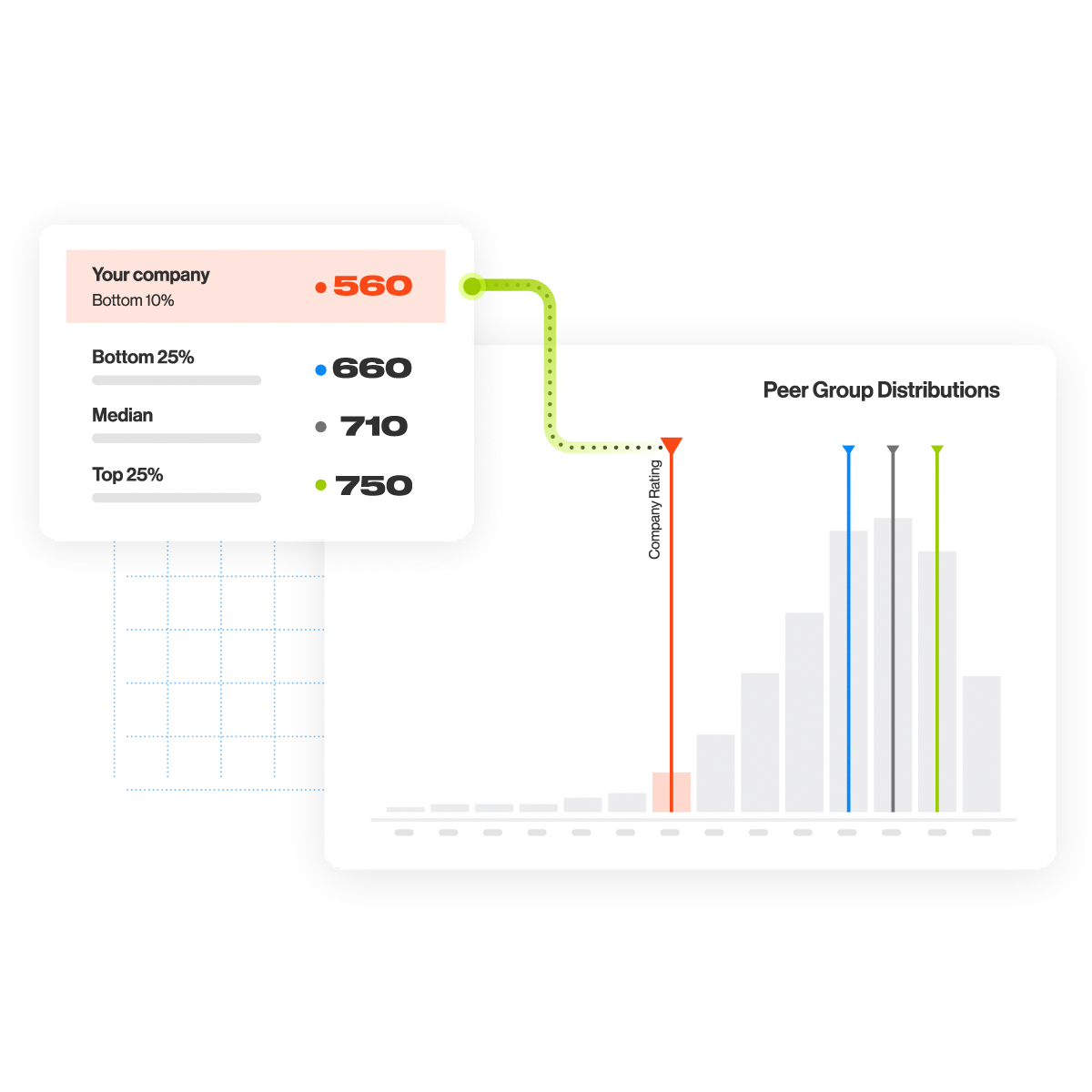
Security Performance Management
Set goals and take action
Take the guesswork out of analyzing performance and setting program goals with metrics based on your own cybersecurity needs and risk tolerance with advanced analytics.
- Compare yourself against meaningful peer groups
- Drill-down into areas of exposure, such as hosting provider, subsidiary, or asset count
- Understand how effective your security controls have been over the last six months
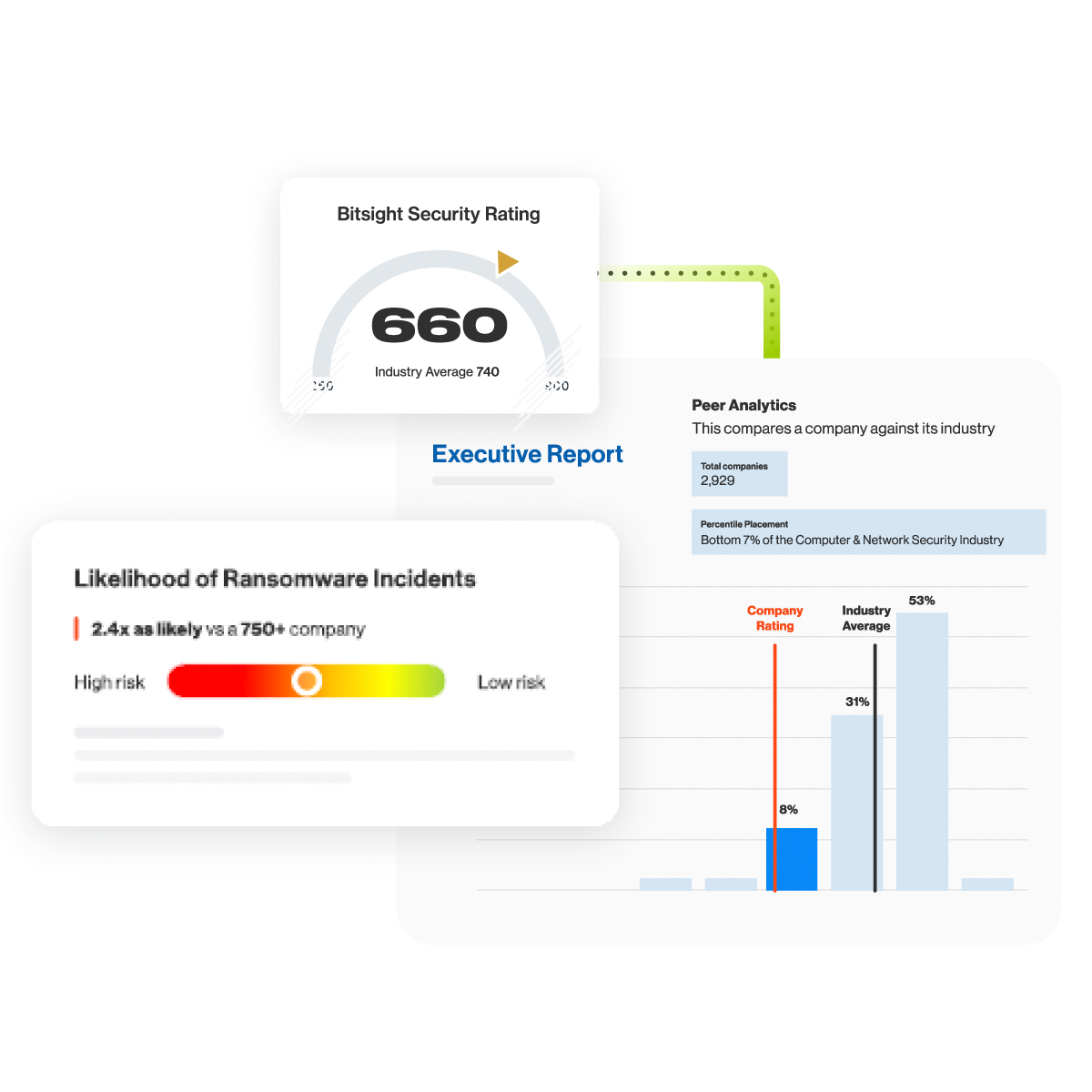
COMMUNICATION, SIMPLIFIED.
Easier reporting. Better buy-in.
No more surface-level metrics. Let stakeholders know how you’re actually doing with security program targets that you can benchmark, map to outcomes, and track over time.
Cyber Governance
Prove that your cyber risk is under control. Align the team around a consistent strategy, get the right context, and track your progress.
Executive Reporting
Bridge the communication gap with digestible metrics that reframe the conversation about cybersecurity into one about business risk.

Quality matters. For data, it matters more.
Bitsight operates one of the largest risk datasets in the world, combining Artificial Intelligence with the experience and knowledge from dedicated technical researchers to map the linkages across entities and provide the most accurate view of your attack surface within our solutions.
We leverage knowledge on millions of entities, continuously updated by researchers to create a unique AI training set. The training set enables us to identify relationships between data sources, assess confidence, and attribute assets at internet scale.
The result is a truly unique view of the internet — and your organization—to offer insights on assets, third-party relationships, vulnerabilities, and other indicators of security diligence to help you effectively manage risk.

Feel Interested? Contact Us For Details.
